What Is Computer Security Explain Threats Of Computer Security
Threats to information and information systems may be categorized and a corresponding security goal may be defined for each category of threats. Inside data breaches are on the rise and companies should have the proper tools and systems in place to detect them.

Social Engineering And How To Win The Battle For Trust Infographic Vasco Data Security Blog Cyber Security Awareness Computer Security Cyber Security
Students looking for careers in information technology risk management cyber defense cyber threats cybercrime digital forensics incident response IT Security computer networking cybersecurity risks information assurance intrusion detection risk assessment security analysis and vulnerability management can all benefit from the material in the courses.

What is computer security explain threats of computer security. In contrast a computers hard disk or SDD is its long-term memory where things are stored more or less permanently. Inside threats must be taken seriously and seen as a real risk by security leaders and tough questions will need to be asked about whether organizations have the proper tools in place to spot and stop them. Using our security programs and services in the manual cleaning of Windows and OS devices we help people every day to have their computer running in the best and safest way.
If your computer is performing a bunch of other. Computer science drives job growth and innovation throughout our economy and society. RAM is your computers short-term memory.
The role primarily investigates responds to and hunts for threats using Microsoft Azure Sentinel Azure Defender Microsoft 365 Defender and third-party security products. Security specialists must explain complex computer issues in laymans terms to help managers. When you watch a video even a simple YouTube video you can fall victim to buffering problems.
Every computing device has RAM whether its a desktop computer running Windows MacOS or Linux a tablet or smartphone or even a special-purpose computing device such as a smart TV. Generally a computer program will have some level of system access to function properly. Cyber Security Threats on the Internet and.
The remainder of the paper is organised. And make up over half of all projected new jobs in STEM fields making Computer Science one of the most in-demand college degrees. Riskware is best understood as programs offering access to special functions at the cost of security or legality.
A security awareness program is a formal program with the goal of training users of the potential threats to an organizations information and how to avoid situations that might put the organizations data at risk. Computing occupations are the number 1 source of all new wages in the US. Avast Forum Discuss with the.
In this article we explain whats happening and show how to stop or. Avast Decoded In-depth technical articles regarding security threats. To begin lets start with why riskware exists and explain how it works.
The goals of the security awareness program are to lower the organizations attack surface. Cyber security firm Archived 3 A pril 2016 at the Way. Wireless mouse leave billions at risk of computer hack.
Bill Gardner in Building an Information Security Awareness Program 2014. A set of security goals identified as a result of a threat analysis should be revised periodically to ensure its adequacy. It also defines the encrypted decrypted and authenticated packets.
With this write-up we have introduced different types of email threats which can affect the users data business or company in a harmful way. Security of a wireless LAN still remains the top concern in the home and corporate network. Reluctance on the part of the organization to adequately prepare staff for making security policy a part of the work environment makes the rest of the effort an exercise in the theoretical--and theory wont protect a system from threats that are all too real see Chapter 10 Training.
Designed to explain. An instruction is an order given to a computer processor by a computer programAt the lowest level each instruction is a sequence of 0s and 1s that describes a physical operation the computer is to perform such as Add and depending on the particular instruction type the specification of special storage areas called registers that may contain data to be used in carrying out the. The IP security IPSec is an Internet Engineering Task Force IETF standard suite of protocols between 2 communication points across the IP network that provide data authentication integrity and confidentiality.
The protocols needed for secure key exchange and key management are defined in it. Our skilled supporters explain the process to you in a way that is easy to understand. Threats to Asset Security Department-Specific Threats to Asset Security Front Office Largest area of security concern is fraudulent selling of rooms Use housekeeping discrepancy report to detect room revenue fraud Housekeeping Guest-theft of housekeeping supplies Theft from guest rooms by room attendants or other employees - best policy is to report the incident to.
Since the Security Operations Analyst consumes the operational output of these tools they are also a critical stakeholder in the configuration and deployment of these technologies. This paper discusses the vulnerabilities and security issues pertaining to the IEEE 80211 security standard and describes major well known attackthreats to the home and enterprise wireless LAN system. One must know about current email security threats that can harm the data and lead to vulnerabilities.
For every person whether a home user or a companys owner security is an important concern. Security specialists must develop problem-solving and critical thinking skills plus the communication skills necessary to liaise with company executives.
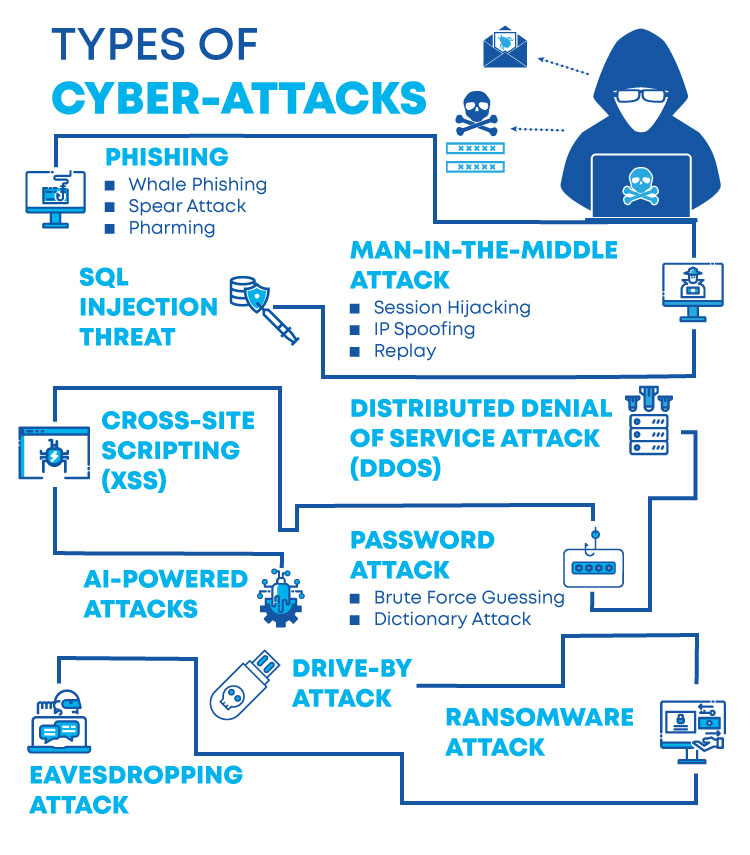
Everything You Need To Know About Cybersecurity Attacks And How To Prevent Them

10 Steps For Enhancing Cyber Security Infographic Swiss Cyber Forum In 2021 Cybersecurity Infographic Cyber Security Cyber Security Technology

What Is Cybersecurity In 2021 What Is Cyber Security Cyber Security Awareness Cyber Security Technology

Pin By Juan On Cybersecurity Cyber Security Cyber Security Threats Cyber Safety

7 Types Of Cyber Security Threats

Security Infographic Gif 625 799 Pixels Cyber Security Awareness Computer Security Security Consultant

28 Infographs Of Beautiful Data Wow Gallery In 2021 Cyber Security Cybersecurity Training Cybersecurity Hacks

Top 9 Cybersecurity Threats And Vulnerabilities

Cyber Security Training Cybersecurity Training Cyber Security Technology Cyber Security Career

Everything You Need To Know About Cybersecurity Attacks And How To Prevent Them


Posting Komentar untuk "What Is Computer Security Explain Threats Of Computer Security"